#nobridge
- 2 Posts
- 69 Comments

- RAID is never a replacement for backups.
- Never work directly with a surviving disk, clone it and work with the cloned drive.
- Are you sure you can’t rebuild the RAID? That really is the best solution in many cases.
- If a RAID failure is within tolerance (1 drive in a RAID5 array) then it should still be operational. Make a backup before rebuilding if you don’t have one already.
- If more disks are gone than that then don’t count on recovering all data even with data recovery tools.

The first thing to check is whether you can install your CAD software on a virtual machine with your current license. If you have good internet at home and already own a CAD machine then it might be easier to setup VPN access and remote control that machine for your Windows needs. Sunshine/Moonlight works good if you have the bandwidth for it.

Interesting that Toshiba/Seagate has best 16TB stats and WDC bad ones in comparison, but for 14TB it’s reversed. My homelab disks apparently has 0.71% risk of dying after 22 months (seagate exos x16 st16000nm001g).
edit: WDC does good in 16TB too, their only outlier there could be due to low number of disks in deive count. And the same is true when checking total no of disks for 14TB.
I can only be another “everyone” and say go for a Synology. If you wanna run services on your NAS then the DSM is a godsend. The 423+ sounds like a good fit, might wanna grab a RAM upgrade for it though.
edit: As you mentioned Jellyfin - if you wanna stream video you definitely want the 423+ and not the 923+ as the AMD Ryzen R1600 lacks GPU to transcode video streams.

Alternatively, you can create new users from the command line.
This can be done as follows:
If synapse was installed via pip, activate the virtualenv as follows (if Synapse was installed via a prebuilt package, register_new_matrix_user should already be on the search path):
cd ~/synapse
source env/bin/activate
synctl start # if not already running
Run the following command:
register_new_matrix_user -c homeserver.yaml
This will prompt you to add details for the new user, and will then connect to the running Synapse to create the new user. For example:
New user localpart: erikj
Password:
Confirm password:
Make admin [no]:
Success!
This process uses a setting registration_shared_secret, which is shared between Synapse itself and the register_new_matrix_user script.
It doesn’t matter what it is (a random value is generated by --generate-config), but it should be kept secret, as anyone with knowledge of it can register users, including admin accounts, on your server even if enable_registration is false.
https://element-hq.github.io/synapse/latest/setup/installation.html

OpenWrt with 802.11r and 802.11s configured will work as a mesh network with roaming functionality.
https://openwrt.org/docs/guide-user/network/wifi/mesh/80211s
https://openwrt.org/docs/guide-user/network/wifi/roaming
Not many Ruckus devices that are supported though:
Brand - Model - Supported Version
Ruckus - ZF7025 - 23.05.2
Ruckus - ZF7321 - 23.05.2
Ruckus - ZF7341 - 23.05.2
Ruckus - ZF7343 - 23.05.2
Ruckus - ZF7351 - 23.05.2
Ruckus - ZF7352 - 23.05.2
Ruckus - ZF7363 - 23.05.2
Ruckus - ZF7372 - 23.05.2
https://openwrt.org/toh/start?toh.filter.supportedcurrentrel=22.03|23.05

Software: OpenWrt - https://openwrt.org/docs/guide-user/network/wifi/roaming
Devices: Supported devices found here - https://openwrt.org/toh/start?toh.filter.supportedcurrentrel=22.03|23.05

pfsense and opnsense are very similar. The pfsense devs has acted like jackasses towards the opnsense gang. They are both great for a router/firewall/vpn device. I would use external access points with them.
I think there are more addons to pfsense than opnsense.
OpenWrt is great when it comes to WiFi, but I find it much less intuitive to use for router/firewall parts. Could be that I am used to the way pfsense and opnsense do things.
Neither do switching from what I know, so pair the router with a switch of your choice.
- @anamethatisnt@lemmy.world to
 English
English - •
- 5M
- •

I consider client devices to be a big risk factor and if I can keep them from having direct access to the Backup NAS and the IoT I consider that a big win. A simple ransomware attack on a client device would find any NFS/SMB shares the client can access and start encrypting - having the Backup NAS on a separate VLAN that only the server can access stops most of those from affecting the backup and makes restoring a lot easier. I would definitely recommend having an offline backup of the NAS as well in case of the server being breached.

If you go for SSD another thing to think about is the TBW on them. Buying a low endurance SSD might save some electricity but will cost more in SSDs over time. Example:
Crucial P3 Plus M.2 NVMe SSD 2TB (2.67W on your link) has 440TBW compared to Kingston Fury Renegade M.2 NVMe SSD Gen 4 2TB (4.92W on your link) with 2000TBW.
Those few watts you save on using the Crucial P3 Plus will be less than the extra cost in buying new SSDs earlier.
The site I checked TBW on has the Kingston Fury at $9.4 more than the Crucial P3 Plus.
I think proper datacenter 3.5’’ HDDs will give you the most efficient Wattage per TB disk space
Seagate Exos X20 Harddisk ST20000NM007D 20TB SATA-600 7200rpm is supposed to have
Power Consumption 5.4 Watt (idle) | 9.4 Watt (random read) | 6.4 Watt (random write)

Regarding management UIs I’m a fan of Cockpit (https://github.com/cockpit-project/cockpit https://cockpit-project.org/)
Regarding management UIs for docker I believe most use either portainer (https://github.com/portainer/portainer https://www.portainer.io/) or dockge (https://github.com/louislam/dockge https://dockge.kuma.pet/).
Regarding Samba most NAS devices simplify it a lot, but it isn’t that complicated to do on Fedora either and once you’ve got it setup it’s not gonna need a lot of tinkering. (https://docs.fedoraproject.org/en-US/quick-docs/samba/)
Whether you invest in a NAS or not I recommend you invest in a USB disk large enough to act as a backup for the storage disks. That’s not an investment for later but one you want right away. And do make certain it takes backups, not replicates data. A popular option is Borg Backup (https://github.com/borgbackup/borg https://www.borgbackup.org/)
If I went for a NAS I would Borg Backup the laptop to the NAS and then use the NAS own backup software to backup to the USB.

If you liveboot Fedora or something with USB - how’s the upload then?
Should be a quick way to determine if it’s software or hardware based.
edit - Seems that others have had upload troubles with latest Proxmox and fixed it by downgrading:
https://old.reddit.com/r/Proxmox/comments/19d0bf7/slow_upstream_thru_proxmox81/

Cockpit
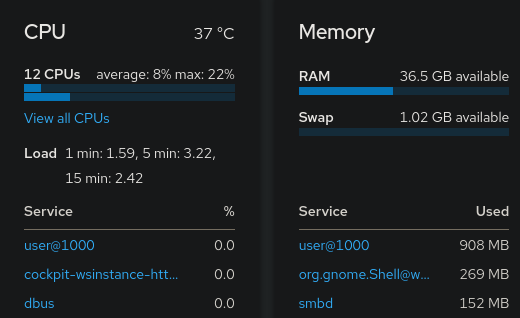
I do know about and use Cockpit with said virtual machine manager but I mostly use it as a shutdown/boot/restart app in my phone and a convenient service monitor and log viewer when troubleshooting.
Wireguard/OpenVPN
I really should try out Wireguard sometime but currently OpenVPN is fast enough for my bandwidth and I was already proficient with setting it up before Wireguard.
The WebUI definitely looks useful.

For linux this is as easy as script <filename>, ex:
[user@fedoragaming ~]$ script 20240313InstallingJellyfin.log
Script started, output log file is ‘20240313InstallingJellyfin.log’.
[user@fedoragaming ~]$ exit
exit
Script done.
edit: and for Windows I recommend using putty, it can also save sessions to logs.

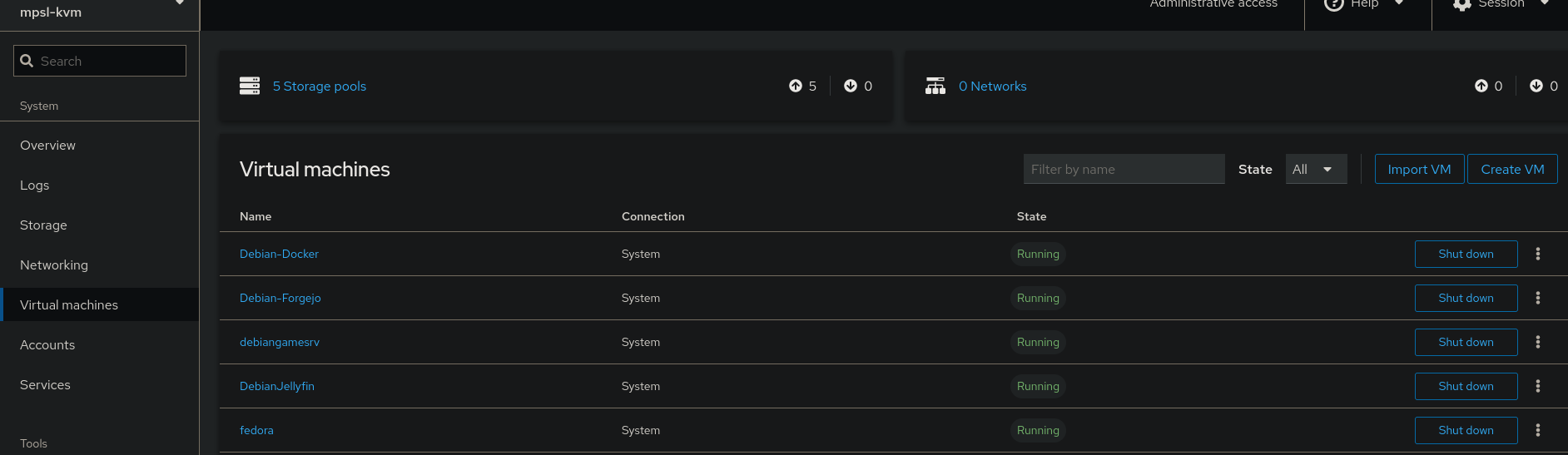
My Debian Hypervisor do have a DE (GNOME) to be able to easily access virtual machines with virt-manager if I mess up their networking, my Debian VMs run CLI only though.
Regarding your last section I agree strongly - I only expose my vpn with no other incoming ports open. You also don’t need to invest in a domain if you do it this way.
I don’t mind helping my friends install their openvpn client and certificate and it’s nice to not have my services bombarded with failed connection attempts.

Basic knowledge that makes selfhosting easier
- Some networking basics (Firewall, VPN, NAT, DHCP, ARP, VLAN) makes every selfhosters life easier.
1b. Your ISP router probably sucks, but you might be able to experiment with some static DHCP at least. I’m a fan of the BSD based routers opnsense/pfsense but depending on what router you have you might also be able to run OpenWrt on your existing router. - Some management system and filesharing basics (NFS, SMB, SSH, SCP and SFTP).
- Learning how to set up a backup for your stuff. The hypervisor you choose may or may not have a built in solution.
- Checking out a few different hypervisors (Proxmox, Incus, KVM/QEMU, etc) and find out which one you wanna dive deeper into.
4b. Learn how to make a snapshot for easy rollback in said hypervisor ASAP. Being able to undo the last changes that broke a machine is a godsend.
4c. VM, LXC, Docker and Podman basics (what are they, how do they differ, which one fits my usecase?)
I know Flackbox has a good CCNA (networking) study guide on youtube, but that is way too in depth for a self hosting beginner.
Here’s some introduction to different parts of the network:
Free CCNA 200-301 Course 06-05: IPv4 Addresses
Free CCNA 200-301 Course 23-01: DHCP Introduction
Free CCNA 200-301 Course 12-04: ARP Address Resolution Protocol
Free CCNA 200-301 Course 21-01: VLANs Introduction
Free CCNA 200-301 Course 21-04: Why we have VLANs

Material Files support both SMB and SFTP - https://f-droid.org/en/packages/me.zhanghai.android.files/

Any router that supports latest openwrt will be able to do a mesh network, if you have the option to run cable I would recommend ethernet backhaul instead.
Sometimes there are caveats when setting up the mesh, f.e. the firmware issue and fix here:
https://www.tekovic.com/blog/openwrt-80211s-mesh-networking/
Hardware list:
https://openwrt.org/toh/start?toh.filter.supportedcurrentrel=22.03|23.05
edit:
OpenWrt Mesh guide:
https://openwrt.org/docs/guide-user/network/wifi/mesh/80211s
https://openwrt.org/docs/guide-user/network/wifi/mesh/mesh11sd
edit 2 adding the openwrt warning here:
It is unfortunate that some manufacturers have used the word “Mesh” for marketing purposes to describe their non-standard, closed source, proprietary “roaming” functionality and this causes great confusion to many people when they enter the world of international standards and open source firmware for their network infrastructure.
The accepted standard for mesh networks is ieee802.11s.
The accepted standard for fast roaming of user devices is ieee802.11r.
These are two completely unrelated standards.

The main config needed is AP+Sta mode, which is explained here:
https://openwrt.org/docs/guide-user/network/wifi/ap_sta

Pretend the “main router” is a hotel wifi and use the TravelMate package.
https://github.com/openwrt/packages/blob/master/net/travelmate/files/README.md
You setup Proxmox Backup Server on separate hardware and then you add it as a storage option in your Proxmox Virtualization Server.
I haven’t dived into it but I imagine you could run the Proxmox Backup Server as a VM in your Synology NAS.
https://www.proxmox.com/images/download/pbs/docs/proxmox-backup-3-1.pdf
edit: Unofficial PBS Docker github: https://github.com/ayufan/pve-backup-server-dockerfiles

There’s also some web-based solutions but not sure setting up a webserver is any less complicated than using docker:
https://lycheeorg.github.io/
https://piwigo.org/

Found an interesting read regarding the matter here:
https://old.reddit.com/r/ceph/comments/mppwas/single_node_ceph_vs_zfsbtrfs/
Most seem to recommend going for ZFS instead if using a single machine but there is a person discussing his first hand experience with single node Ceph.
Eatons batteries are usually really simple to switch, see
https://www.eaton.com/content/dam/eaton/products/backup-power-ups-surge-it-power-distribution/backup-power-ups/eaton-5s-ups/eaton-5s-120v-user-manual-700-1000-1500-lcd.pdf
For me they are meant for allowing a graceful shutdown in a powerout scenario and to protect the hardware behind them from power surges.

Isn’t the solution to send them this link? ;-)
https://distrowatch.com/dwres.php?resource=major
- @anamethatisnt@lemmy.world to
 English
English - •
- 9M
- •

Yeah, if there’s a full system failure without any backups and no option to get the system operational again then I would land in clone the drives before trying to restore data from them.