

- 4 Posts
- 108 Comments


Yes you can do that. I do with opnsense. The username and passwd are not obvious though - they’re probably not what you use to login to the ISP portal with.
Most ISPs will have a brief FAQ on how to use third party equipment with the basics of what settings are important for your connection. You just need to enter them in to pfsense correctly. Also, sometimes searching for “<ISP_name> pfsense” can find useful blogs and articles.


It’d be nice if email clients automatically checked for public keys for any email you enter in the To fields. With a nice prompt that keys have been found to Encrypt the message with. It doesnt sound too difficult and it could lead to much wider adoption of secure emails.
Unfortunately most people get their email free because companies like reading it and stopping that means it might become a paid for service. Something I’m happy to pay for, but many wouldn’t be.

 English
English- •
- wiki.gnupg.org
- •
- 2M
- •
Run your own DNS server on your network, such as Unbound or pihole. Setup the overrides so that domain.example.lan resolves to a local IP. Set your upstream DNS to something like 1.1.1.1 to resolve everything else. Set your DHCP to give out the IP of the DNS server so clients will use it
You don’t need to add block lists if you don’t want.
You can also run a reverse proxy on your lan and configure your DNS so that service1.example.lan and service2.example.lan both point to the same IP. The reverse proxy then redirects the request based on the requested domain name, whether that’s on a separate server or on the same server on a different port.


I don’t understand it either. On one hand people say don’t remember addresses, use DNS and on the other DNS relies on static addresses but then every device is “supposed” to have random addresses via SLAAC or privacy addresses. It just doesn’t seem to tie together very well, but if you use them like IPv4 addresses you’re apparently doing it wrong.


I highly recommend watching this guys videos on his analysis of the backblaze data https://www.youtube.com/watch?v=IgJ6YolLxYE&t=1
And a comparison of the difference WD drive colours, which might not be what you expect https://www.youtube.com/watch?v=QDyqNry_mDo&t=2
I’ve been running 3CX for a couple of years with a Voicehost trunk configured. I found it much simpler than free PBX to setup and maintenance has been a breeze. There’s apps or a web based option too. 3CX can be a little picky with older unsupported hardware - the old Cisco phone I bought was a tricky setup, but the Yealink I have phone was plug and play easy.
The tricky bit was configuring the opnsense router and firewall to correctly handle all the ports properly, but I think that’d be the same for any solution and for an internal only option probably not required.


I mean it happened to be mail, but it could have been any service on a server without enough resources. Just bad luck for me this time.
Setting up the mail server was a bit of a pain, but so was setting up a lemmy server. For 6 years it really has been plain sailing. So I was due a change in fortune, I guess

 English
English- •
- 6M
- •


NFS:Heat. Picked it up for only a couple of quid ages ago but have recently started to enjoy it. When i first got it it didn’t run all that well on Proton, but now it is silky smooth. There’s a real sense of speed as the camera moves about. I’m just about getting the hang of the drift mechanic and making some good progress. It’s quite a lot of fun really.


It wouldn’t matter to them really. Just look at how many people have gmail accounts.
They don’t even have to send the whole messages back to base. They could be categorizing your messages in to themes and sending that back to base as small category flags. Use that to build a profile on you and use those for advertising to you.
You mention something on the theme of ‘broken boiler’ in a message, that gets analyzed on the client in to a category of ‘interest in heating / boiler repair’, plus some adjacent categories based on your demographic. The categorization gets sent back and the next website you visit has an ad for British Gas boiler repair.


Well you type messages in in plain text and they decrypt it to show you the messages at the other end. So they can do the nefarious processing on the client side and send back results to the mother ship. E2EE is only good when you trust the two ends, but with WhatsApp and Messenger you shouldn’t trust the ends.


I probably have more accessible from outside than not. Many are required: hosting a website, a media server I can access from anywhere outside the house, my phone system, etc. Some I used to use more than I do now: podcast service, that sort of thing. Then a bunch that are internal only. My phone connects home over Wireguard so that’s pretty convenient when out and about for accessing internal only systems.

 English
English- •
- 1Y
- •

 English
English- •
- lemmy.fwgx.uk
- •
- 1Y
- •
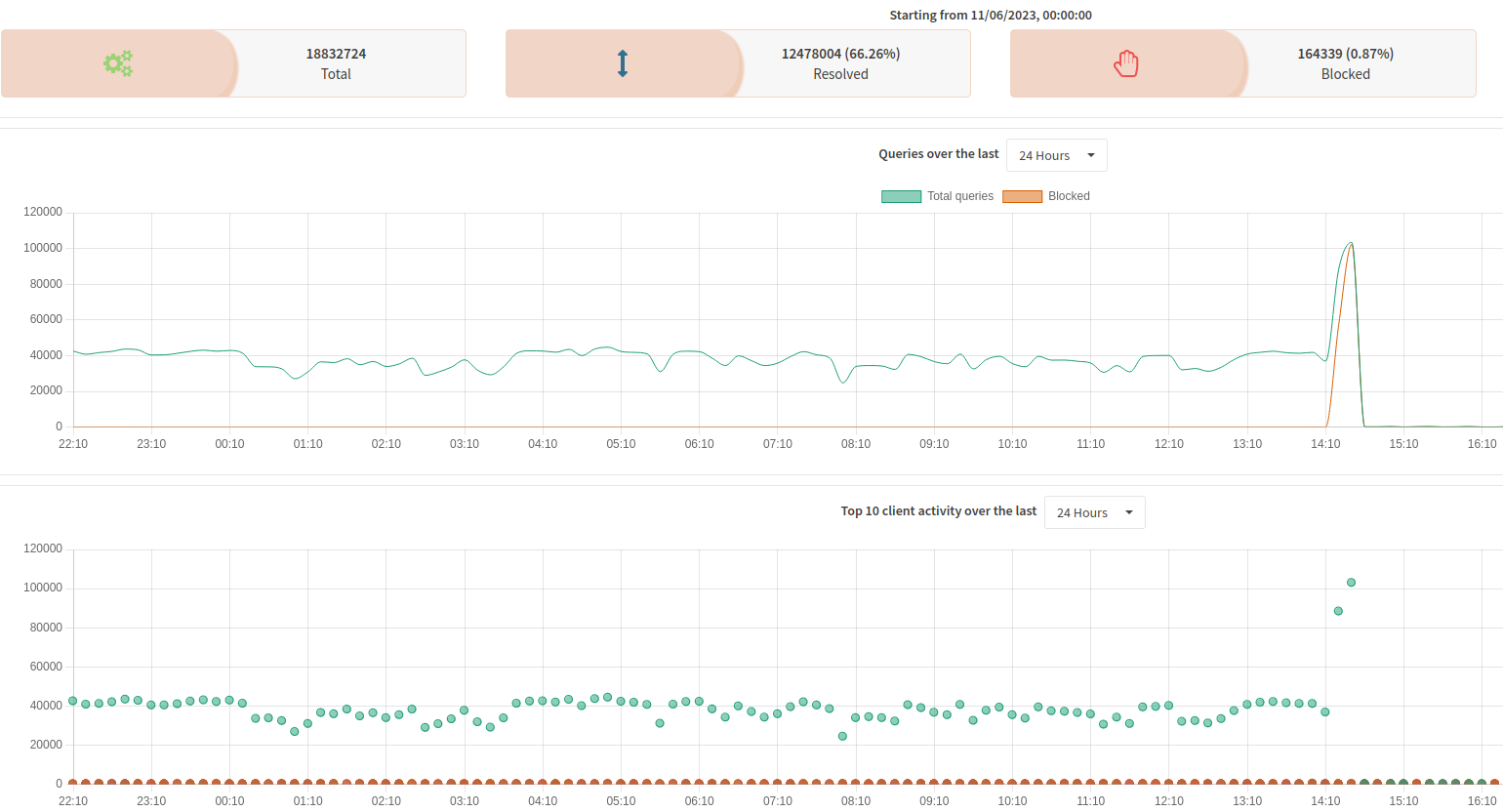
So it’s a vulnerability that requires you to.already have been compromised. Hardly seems like news.
I can understand AMD only patching server chips that by definition will be under greater threat. On the other hand it’s probably not worth the bad publicity not to fix more.